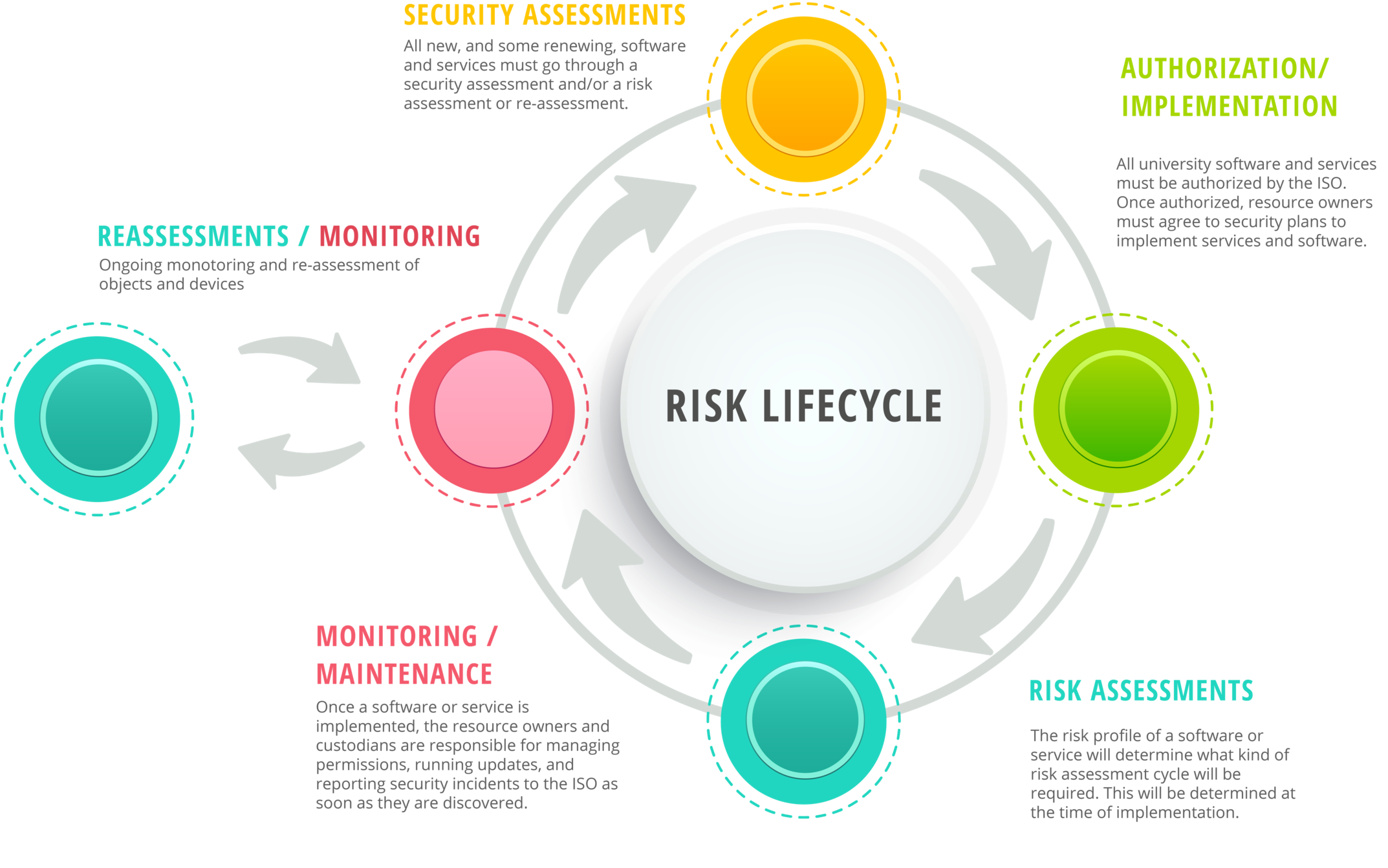
Risk Management Lifecycle
Overview
The Information Security Office facilitates formal, ongoing risk assessments for software, services, and other high-value information resources that need a regular security check-up. Security Assessments and Risk Assessments help assess, document, and manage security risks posed to university information resources. Each serve a different purpose in the risk management lifecycle.
Security Assessments
Security Assessments are conducted by the ISO before things like systems, services, and software are set up and put into use. The ISO reviews information about how a service will be used, what data it will handle, how it can protect that information, and what risks it may present to the university. The ISO then creates a data security plan to help ensure the service can be used safely. Security Assessments are also performed as needed for reasons including: changes in services, updates to service agreements, and changes to law or policy.
Risk Assessments
Risk Assessments are a separate process from Security Assessments. Risk Assessments are completed by Information Resource Owners and Custodians to provide the ISO with up-to-date information about status of certain details and safeguards for existing information systems. Participation in Risk Assessments is required by university policy and state law.
-
General FAQs
-
What’s the difference between a Security Assessment and an Risk Assessment?
Security Assessments are conducted by the Information Security Office, usually before a product, application, or service is used to make sure it can be implemented securely. Risk Assessments are primarily completed by the owners and custodians of information resources on a recurring basis to make sure the resources are still secure and to compare their security posture to that of other resources.
-
Why are some services prohibited for use?
Some products are offer a feature lineup similar to in-place services offered by IT, and where there’s redundancy, there isn’t much incremental benefit for the risk that comes with those duplicated services. In other cases, Texas State doesn’t have a business-to-business agreement with the service provider, so there’s neither contractual protection for the information that it may handle nor an ability for effective, enterprise-grade management, support, and oversight.
-
We haven’t had problems before. Why does the ISO need to assess my department’s services and run risk assessments?
University policy, state laws that drive policy creation, and best practice all require that the Information Security Office assesses products prior to procurement or use. The same policies and practices require that the ISO facilitate ongoing risk assessments for the university's information systems so the risks posed by their use can be measured and mitigated as appropriate.
-
Are service evaluations and risk assessments required for departments outside of IT?
Yes, both Security Assessments and Risk Assessments are required by university-level policy.
-
Are Security Assessments and Risk Assessments required for grant-funded operations and research?
Yes, both Security Assessments and Risk Assessments are required by university-level policy. Teams under the Office of Research and Sponsored Programs may also require additional procedures that involve the ISO to help ensure the goals of a grant or project can be met while protecting the information involved.
-
-
Security Assessments FAQs
-
I’ve used this product for years. Why is the Security Assessment form only required now?
Even though the Information Security Office has conducted security assessments, it is possible that your product has not been brought to the attention of the ISO for assessment. Historic acquisitions may have been assessed under different criteria, or the way in which they were acquired may have prevented the ISO from learning about it until later.
-
Why do I have to fill out the “new” Security Assessment request form when renewing software?
The request form helps provide the ISO and other teams with accurate information about how you or your department use the software or service, including the types of data involved and how many users there will be.
-
I need to get this product yesterday. Can the assessment go any faster?
If a request is particularly urgent, please let the ISO know. Some parts of the review can be expedited based on requesters’ timelines; however, some portions rely on vendors’ diligence and willingness to provide the information needed to conduct the assessment.
-
This product is free; do I still need a Security Assessment?
In most cases, yes, if for nothing else than product and risk inventory purposes. Free and/or open-source products often come with terms of use that could have negative consequences for the university. Unfortunately, even free products have the potential be the cause of a major incident.
-
What’s a HECVAT, and why do I need request one from my vendor?
Developed by members of EDUCAUSE, the HECVAT (short for “Higher Education Cloud Vendor Assessment Tool”) is a standardized self-assessment intended for vendors to complete for prospective, higher-education customers. The HECVAT is intended to provide the ISO nearly all the information needed to assess a vendor’s security posture to help ensure it’s an appropriate tool for the job and place for the data it will handle. More information about the HECVAT is available at https://educause.edu/hecvat.
-
My colleague uses this same software in their department, so why do I need to fill out the form?
Just as different departments have different business processes, they may also use software and services differently from one another. Contextual information, including classification of data that will be stored, processed, and/or transmitted, can make a big difference in whether a product can be authorized and what risks it may pose. In other words, something authorized for handling small volumes of public information may not have a security posture commensurate to high volumes of confidential data.
-
Do I have to be sure I want to buy or use a service for the ISO to assess it?
No, the ISO can begin a security assessment at any time in your selection process well ahead of a purchasing decision being made. If a department is still narrowing their field of options, the ISO would prefer to assess only the front-runners to prevent wasted time and efforts.
-
Do Security Assessments cost my department any money?
No, the ISO does not charge back for Security Assessments.
-
-
Risk Assessment FAQs
-
How can I access Beacon?
Go to the Beacon login page and use the "SAML Authentication" button to log on with your NetID and password via Single Sign-On (SSO). Beacon is only accessible from the campus network and the Remote Access VPN portal.
-
Why do I need to participate in risk assessments? Can’t the ISO answer the risk assessment questions instead?
State administrative code (Texas Administrative Code 202.72.1.A.H and 202.75) requires that information resource owners participate in risk assessments of the resources for which they are responsible. The ISO helps facilitate this process through formalized Risk Assessments and the Security Assessment process, but the ISO cannot answer resource-specific questions on behalf of information resource owners.
-
Someone from IT helped me set up this service. Can they do this risk assessment instead?
Information resource owners are required to participate in the risk assessment process. Formal and informal (university-employed) information resource custodians may, however, assist with answering questions and providing background information. The ISO can also help provide clarification as necessary.
-
Can the questionnaire be assigned to my vendor, cloud-service provider, or other external party?
No, but Information Resource Owners and Custodians may contact relevant external parties on an as-needed basis to get answers to specific questions about the information security system being assessed.
-
I’m not the right person in my department to be running this Risk Assessment. What do I do?
Please contact the ISO as soon as possible at InfoSecGRC@txstate.edu so documentation can be updated and the proper contact identified.
-
My service is running in one of IT’s data centers. Does it still need a Risk Assessment?
This answer depends on many factors, including the type and volume of information handled by your service, as well as the impact an incident related to it could have on the institution. Nonetheless, if you have been identified as a risk assessor, your participation is almost certainly required.
-
Can I reschedule this risk assessment?
Risk assessments must be completed by the stated end date to facilitate institutional reporting requirements. If you are concerned about being able to complete your assessment(s), please contact the ISO at InfoSecGRC@txstate.edu with information about exigent matters or extenuating circumstances.
-
My system has been used for years and hasn’t needed a risk assessment. Why do I need one this year?
There are a few possible reasons. A formal Security Assessment may not have been previously conducted, or the risk presented by your product may have changed relative to other contemporary services.
-
This service was decommissioned. Does it still need a risk assessment?
The questionnaire sent to you via Beacon will accommodate the decommissioning of an information system.
-
What happens with this information?
Information gathered by ongoing risk assessments are used by the ISO to gain a broad, quantifiable image of the security risks presented to the university and to address one-off findings as well as potential “hot spots” that may be common across the institution. Information about these security risks is also reported in varying detail to the university’s President, the Vice President of IT, and the rest of the president’s cabinet, along with the State’s Department of Information Resources.
-
Can I request more frequent risk assessments?
Absolutely. Please contact InfoSecGRC@txstate.edu with your request.
-
Can risk assessments be set up for a service, system, network, location, or computer that hasn’t needed one before?
In almost every case, yes. Please contact InfoSecGRC@txstate.edu with your request and more information about the assessable objects for which ongoing risk assessments should be scheduled.
-