This guide covers tools and strategies for research data, including institutionally authorized software and best practices. This should not be considered comprehensive and a data security plan may still be necessary for your research. Please contact us at infosecurity@txstate.edu if you have questions.
Research Security Guide
Moving forward as an emerging research university, properly securing research data is of the highest regard. Texas State University researchers and employees must value the integrity of any research on campus and ensure data security. To ensure this, Texas State University follows TAC 202 and implements UPPS policies to properly securing the transmission and storage of data. If researchers are unsure of how to properly classify data, they can refer to our Data Classification page and our Policies page to understand Texas State University standards.
Security Principles
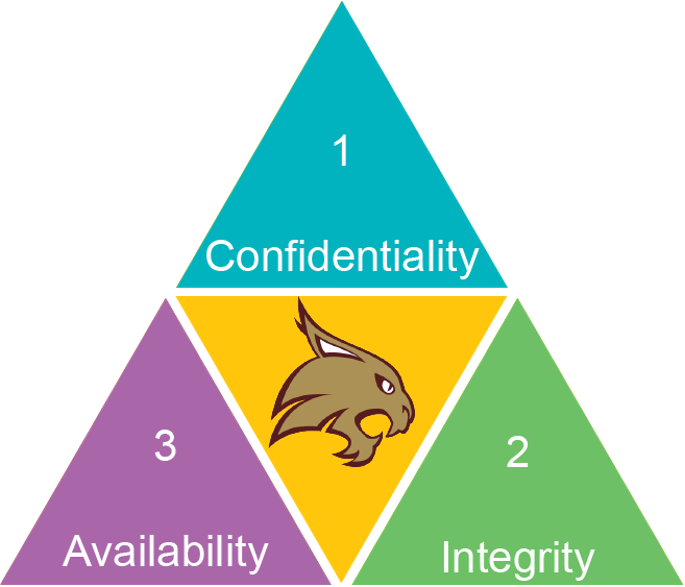
Security philosophy - the C.I.A. triad
The C.I.A. triad is the unifying philosophy for information security policies and practices. These considerations should be at the core of process development for collecting, managing, and storing data in all university research. The C.I.A. triad is defined as follows:
- Confidentiality: Data are only accessed by those who should have access.
- Integrity: Data are known to be accurate and uncorrupted.
- Availability: Accurate, uncorrupted data are available to approved individuals when needed.
What it means to protect data
The protection of data is not an abstract concept with hypothetical implications. There are real-world threats and vulnerabilities that researchers need to be aware of in order to protect their data. The goals of these practices are to ensure the following:
- Maintain Research Integrity - Research findings aren’t called into question because of corrupted data
- Ensure Research Confidentiality - Data is not exposed and test subjects are protected from risk of harm
- Continuous Research Availability - University network is more reliable than personal or removable storage devices
Retention Requirements
Depending on the data type, faculty sponsors of student projects may be required to assume retention responsibilities for their students’ projects. Researchers, particularly project PIs, are responsible for ensuring that records related to their projects are retained for at least as long as required by the university’s Records Retention Schedule.
Data Classification
Data classification is the starting point for developing good security practices for research projects. The types of data being dealt with and the classification of those data will inform the kinds of tools researchers use, how permissions are granted or revoked, how long data must be retained, and what kinds of extra security measure may need to be implemented.
The term "research data" can have wildly different meanings to different disciplines, and research data can present varying risks to data subjects, researchers, and the institution. University policy classifies unpublished research as sensitive information, unless the data contain information that is classified as confidential. These blanket classifications convey a risk-averse stance that is intended to protect the confidentiality of the subject data.
Data Minimization
The concept of reducing the need for data beyond what you need to collect, and collecting the least risky data points possible. Keep data minimization in mind when planning research projects.
For example: an age range is less risky than collecting someone's specific age, which is less risky than collecting someone's exact date of birth.
Age range > Specific age > exact DOB
Research Security Considerations
When conducting research, asking some basic questions about what data is actually needed will help reduce risk. Ask yourself the following questions and consider the following recommendations for reducing risk to research data.
Two questions to ask yourself:
- Do I need to store this data?
- Do I need to transmit this data?
If a clear need for a data point or set is identified then it is better to not collect it. Simultaneously, researchers should endeavor, whenever possible, to reduce the risk level of data collected by following data minimization principles.
Consider the following to reduce risk:
- Identify specific need to transmit or store confidential data
- Find the most appropriate way to transmit or store data Develop a process to reduce storage and transmission
- Redact or use non-PII identifiers like NetID, see the HIPAA guide on de-identification for more information.
Collection & Storage
Principle of Least Privilege
The principle of least privilege refers to an information security concept in which a user is given the minimum levels of access – or permissions – needed to perform their job functions. The principle of least privilege is a cybersecurity best practice, a fundamental step in protecting privileged access to high-value data and assets.
Apply the principle of least privilege when designing your research systems, using the university-authorized services listed in this section.
Data Storage Tools
- Encrypted internal hard drive: university-issued machines
- Restricted-Access files - Department Share Drive (S:Drive)
- UDrive - personal cloud storage
- M365 suite - OneDrive
- M365 suite - SharePoint
- M365 suite - Microsoft Stream
- M365 suite - Microsoft Stream
- MediaFlo
- Code42 CrashPlan
- Canvas Project Sites
